BSNL ISP injects illegal ad scripts
Bharat Sanchar Nigam Limited(BSNL) is an Indian State-owned telecommunication company. I've been using their service for quite a long time, because they were the first & major telecom service provider then, 16 years ago,.. when I bought my first telephone connection and internet service. Through out the association with them, there were many complaints & issues around how they were lazy attending to the customer service requests, took too long for simple Issue resolution, poor technical knowledge exhibited by their broadband customer support team etc., so on. But I was holding on to them, as it didn't cause any major risk or hurdle because that is how most government service usually work over here and I was used to it.
But recently, there were few incidents that have forced me to re-think about changing the ISP.
Incident 1: Hijacking user sessions abruptly
The way they hijack the ongoing session and show their FUP(Fair Usage Policy) limit reached message is un-professional. Think ., In-case you are in-between an important transaction and then this BSNL message hijacks the session OFF from your on-going transaction. That is totally rude way to alert a customer.
Incident 2: Illegally injecting AD scripts on random unsecured(HTTP) websites
I have seen strange AD popups and redirects,.. ON and OFF while using BSNL broadband service. My father have complained many times about software that prompt him to download and run system scan.
I usually suspected & blamed the website owners or chrome browser add-on/extension developers for this behaviour. But, for last few weeks this behaviour has started to occur more often and totally intrusive during web browsing sessions. The behaviour is as follows
When I visit some HTTP website/blog and try to click/copy/navigate on any part of the website. It simply hijacks my click and opens up a strange/un-related website,.. which then redirects me to a malware website or Adware sites or some times to eCommerce sites like Snapdeal or Flipkart..,
So I started investigating by looking into the Chrome Developer Tool script source locations. It showed me that certain scripts are served from the IP address with non-default port numbers.
e.g.,
http://61.0.245.90:3000/api/getnoti?tm=1539446276288&subscriberId=cG00NDI1OTkwMTc4X3NjZHJpZEBic25sLmlu&subscriberIP=117.193.70.5&nadipdata=%22%7B%5C%22url%5C%22%3A%5C%22%2Fpagead%2Fjs%2Fadsbygoogle.js%5C%22%2C%5C%22referer%5C%22%3A%5C%22http%3A%2F%2Fsforsuresh.in%2Fmysql_varchar_max_length%2F%5C%22%2C%5C%22host%5C%22%3A%5C%22pagead2.googlesyndication.com%5C%22%2C%5C%22categories%5C%22%3A%5B0%5D%2C%5C%22reputations%5C%22%3A%5B1%5D%2C%5C%22nadipdomain%5C%22%3A10000%7D%22&screenheight=864&screenwidth=1536&preadid=-1&cycle=false&_=1539446274066
http://61.0.245.90:3000/getjs?nadipdata=%22%7B%22url%22:%22%2Fpagead%2Fjs%2Fadsbygoogle.js%22%2C%22referer%22:%22http:%2F%2Fsforsuresh.in%2Fmysql_varchar_max_length%2F%22%2C%22host%22:%22pagead2.googlesyndication.com%22%2C%22categories%22:%5B0%5D%2C%22reputations%22:%5B1%5D%2C%22nadipdomain%22:10000%7D%22&screenheight=864&screenwidth=1536&tm=1539446273323&lib=true&fingerprint=c2VwLW5vLXJlZGlyZWN0That was quite scary because
- the content within the scripts are encoded for normal eyes,.. probably for a reason.
- there is a tracking pixel i.e.,
1x1.pngis sent to 117.205.13.171. Like a hidden camera on what I visit... This is damn too scary.
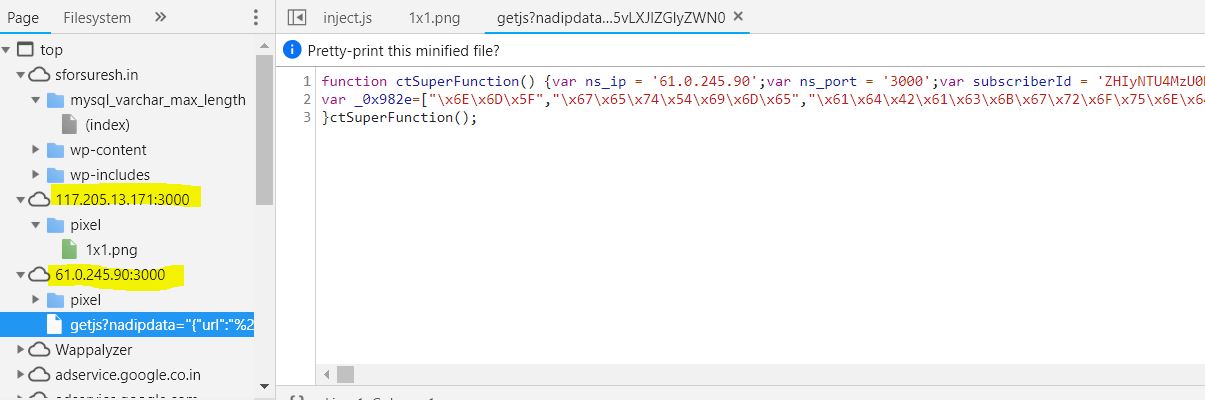
The file was obfuscated using encoded hexa-characters,. So I've to use an online UnObfucator to decode the script.
After decoding, the script showed me few terms that revealed its intention about displaying ads - how and when to push i.e., slide or fixed or top position etc., with different AD providers / media they use.
Then few terms about usage tracking - `metric`, `1x1 Pixel tracker`, `referrer`, IP address etc., Is it a complete hidden surveillance by my telecom providers?
var _0x982e$jscomp$0 = ["nm_", "getTime", "adBackground", "block", "ready", "length", "#", "type", "BANNER", "OVERSLIDE", "TOP_AD", "FLOORAD", "FIXED", "repeat", "INTERSTITIAL", "INTERSTITIAL_FLASH", "CUSTOMIZED", "CUSTOMIZED_DYNAMIC", "NEW_TAB", "IFRAME", "SURVEY", "SURVEY_IMAGES", "VIDEO", "VAST", "IMA", "KOMLI_BANNER", "INMOBI", "MOBVISTA", "ADATHA", "SODAMEDIA", "ADMAVEN", "ADCASH", "ADCASH_BANNER", "NONE", "ADSTERRA", "ADSUPPLY", "ADVORTEX", "PROPELLER", "BID_MAGNET", "GALAKSION", "CLICKADU",
"YEPMEDIA", "ADMEDIA", "PIXEL", "loadAdDefaultOnSwitch", "Default type no configurado", "Existe div con id ", ". referer: ", "href", "location", "loadAd", "undefined", "http://", "host", "_blank", "open", "focus", "Please allow popups for this website", "url", "substr", "/", "srcurl", "?", "indexOf", "&tm=", "&subscriberId=", "&subscriberIP=", "&domainName=", "hostname", "&adId=", "adid", "&viewKey=", "viewKey", "stringify", "position", "adwidth", "adheight", "removescrollbody", "true", "backgroundblack",
"createElement", "src", "setAttribute", "id", "allowFullScreen", "", "width", "style", "height", "fixed", "border", "none", "overflow", "hidden", "margin", "0 auto", "zIndex", "display", "padding", "0px", "FULLSCREEN", "top", "px", "left", "%", "innerWidth", "clientWidth", "documentElement", "body", "TOP", "BOTTOM", "bottom", "CENTERED", "innerHeight", "clientHeight", "firstChild", "insertBefore", "appendChild", "getElementsByTagName", "div", "(src=", "): document.body is ", "loadIframeAd", ":",
"/nadip/iframe/survey?", "tm=", "loadSurveyAd", "/nadip/iframe/surveyimages?", "loadSurveyImagesAd", "horizontalposition", "/nadip/iframe/video?", "subscriberId=", "&refererURL=", "&domain=", "replace", "&adWidthxHeight=", "x", "&userAgent=", "LEFT", "RIGHT", "right", "loadVideoAd", "loadVastAd", "100%",
...
];You can check-out the complete JavaScript in this gist.
The intention behind the script was well showcased in the decoded script. So, I've continued further to see from where these scripts are being served and who is responsible for it.
Source: whois.apnic.netIP Address: 61.0.245.90
% [whois.apnic.net]
% Whois data copyright terms http://www.apnic.net/db/dbcopyright.html
% Information related to '61.0.245.88 - 61.0.245.95'
% Abuse contact for '61.0.245.88 - 61.0.245.95' is 'abuse@bsnl.in'
inetnum: 61.0.245.88 - 61.0.245.95
netname: AMPL-SERVER-STR-HRD
descr: AMPL SERVER STR HRD
descr: 3rd floor STR , Haddows road
descr: Nungamabakkamm chennai - 600034
descr:
admin-c: VV348-AP
tech-c: VV349-AP
country: IN
admin-c: NIC3-AP
admin-c: NC83-AP
tech-c: CDN1-AP
mnt-by: MAINT-IN-DOT
mnt-irt: IRT-BSNL-IN
status: ASSIGNED NON-PORTABLE
last-modified: 2017-08-23T06:38:02Z
source: APNIC
irt: IRT-BSNL-IN
address: Internet Cell
address: Bharat Sanchar Nigam Limited
address: 8th Floor,148-B Statesman House
address: Barakhamba Road, New Delhi - 110 001
e-mail: abuse@bsnl.in
abuse-mailbox: abuse@bsnl.in
admin-c: NC83-AP
tech-c: CGMD1-AP
auth: # Filtered
mnt-by: MAINT-IN-DOT
last-modified: 2017-10-20T05:42:50Z
source: APNIC
role: CGM Data Networks
address: CTS Compound
address: Netaji Nagar
address: New Delhi- 110 023
country: IN
phone: +91-11-24106782
phone: +91-11-24102119
fax-no: +91-11-26116783
fax-no: +91-11-26887888
e-mail: dnwplg@bsnl.in
e-mail: hostmaster@bsnl.in
admin-c: CGMD1-AP
tech-c: DT197-AP
tech-c: BH155-AP
nic-hdl: CDN1-AP
mnt-by: MAINT-IN-DOT
last-modified: 2016-10-01T09:10:26Z
source: APNIC
role: NS Cell
address: Internet Cell
address: Bharat Sanchar Nigam Limited
address: 8th Floor,148-B Statesman House
address: Barakhamba Road, New Delhi - 110 001
country: IN
phone: +91-11-23734057
phone: +91-11-23710183
fax-no: +91-11-23734052
e-mail: hostmaster@bsnl.in
e-mail: abuse@bsnl.in
admin-c: CGMD1-AP
tech-c: DT197-AP
nic-hdl: NC83-AP
mnt-by: MAINT-IN-DOT
last-modified: 2016-10-01T09:05:15Z
source: APNIC
person: Node Incharge CHENNAI
nic-hdl: NIC3-AP
address: NIB CHENNAI
address: 20 Hadoows Road Second Floor,Haddows Road Telephone Exchange,Chennai 6
phone: +91-044-28202299
fax-no: +91-044-28204646
country: IN
e-mail: nib_chennai@sancharnet.in
mnt-by: MAINT-IN-PER-DOT
last-modified: 2008-09-04T07:31:40Z
source: APNIC
person: VIJAY VIJAY
nic-hdl: VV348-AP
address: 3rd floor STR , Haddows road
address: Nungamabakkamm chennai - 600034
address:
phone: +91-9649466325
fax-no: +91-44-28270247
country: IN
e-mail: vijay@abeermedia.com
mnt-by: MAINT-IN-PER-DOT
last-modified: 2017-08-22T11:36:01Z
source: APNIC
person: VIJAY VIJAY
nic-hdl: VV349-AP
address: 3rd floor STR , Haddows road
address: Nungamabakkamm chennai - 600034
address:
phone: +91-9649466325
fax-no: +91-44-28270247
country: IN
e-mail: vijay@abeermedia.com
mnt-by: MAINT-IN-PER-DOT
last-modified: 2017-08-22T11:36:01Z
source: APNIC
% Information related to '61.0.240.0/20AS9829'
route: 61.0.240.0/20
descr: BSNL Internet
country: IN
origin: AS9829
mnt-lower: MAINT-IN-DOT
mnt-routes: MAINT-IN-DOT
mnt-by: MAINT-IN-AS9829
last-modified: 2008-09-04T07:54:45Z
source: APNIC
% This query was served by the APNIC Whois Service version 1.88.15-46 (WHOIS-US3)WhoIs log on IP address -`61.0.245.90` showed that the scripts are served from the box that sits within BSNL office in Nungambakkam, Chennai.
Similarly, probing for the information on IP that receives the tracking pixel hits the Broadband MultiPlay Project, Bangalore.
Source: whois.apnic.netIP Address: 117.205.13.171
% [whois.apnic.net]
% Whois data copyright terms http://www.apnic.net/db/dbcopyright.html
% Information related to '117.203.0.0 - 117.205.255.255'
% Abuse contact for '117.203.0.0 - 117.205.255.255' is 'abuse@bsnl.in'
inetnum: 117.203.0.0 - 117.205.255.255
netname: BB-Multiplay
descr: Broadband Multiplay Project, O/o DGM BB, NOC BSNL Bangalore
country: IN
admin-c: BH155-AP
tech-c: DB374-AP
status: ASSIGNED NON-PORTABLE
mnt-by: MAINT-IN-DOT
mnt-irt: IRT-BSNL-IN
last-modified: 2017-07-25T06:42:04Z
source: APNIC
irt: IRT-BSNL-IN
address: Internet Cell
address: Bharat Sanchar Nigam Limited
address: 8th Floor,148-B Statesman House
address: Barakhamba Road, New Delhi - 110 001
e-mail: abuse@bsnl.in
abuse-mailbox: abuse@bsnl.in
admin-c: NC83-AP
tech-c: CGMD1-AP
auth: # Filtered
mnt-by: MAINT-IN-DOT
last-modified: 2017-10-20T05:42:50Z
source: APNIC
person: BSNL Hostmaster
nic-hdl: BH155-AP
e-mail: hostmaster@bsnl.in
address: Broadband Networks
address: Bharat Sanchar Nigam Limited
address: 2nd Floor, Telephone Exchange, Sector 62
address: Noida
phone: +91-120-2404243
fax-no: +91-120-2404241
country: IN
mnt-by: MAINT-IN-PER-DOT
last-modified: 2015-11-12T06:00:14Z
source: APNIC
person: DGM Broadband
address: BSNL NOC Bangalore
country: IN
phone: +91-080-25805800
fax-no: +91-080-25800022
e-mail: dnwplg@bsnl.in
nic-hdl: DB374-AP
mnt-by: MAINT-IN-PER-DOT
last-modified: 2011-02-19T10:03:44Z
source: APNIC
% Information related to '117.205.0.0/20AS9829'
route: 117.205.0.0/20
descr: BSNL Internet
origin: AS9829
country: IN
mnt-by: MAINT-IN-DOT
last-modified: 2011-01-10T10:42:59Z
source: APNIC
% This query was served by the APNIC Whois Service version 1.88.15-46 (WHOIS-US3)So finally,
Seeing that the my tracking information is just with my ISP, not some foreign hacking community was little consoling. Because literally speaking any telecom provider can simply put a magnetic to record all personal conversations of their subscribers. So compared to that risk, this information tracking was comparatively smaller risk ![]() .
.
Let me complete this post with final message to readers..,
Users:
To prevent this AD script injection related problems, you can opt for any of the following solutions
- You can install AdBlock browser add-on/extension, which can effectively block the AD medias and its requests from the browser. [Please do white-list the valid & legit website ADs, which provides revenue for the web bloggers / contributors. So to keep them and contributing to the community through such post ]
- You can not block these BSNL IP addresses using hosts file, because these IP address doesn't use DNS names. So, you have to use
IP Security policy Managementconsole to define IP filter rule. You can check-out how to do this in Block BSNL ADs using IPSec post. - You can define a firewall block rule and block this out-going requests to the BSNL servers.
- You can simply move-on to another Internet Service Provider, who will be most probably better professionals than these guys.
- Visit just
httpsenabled websites, because Transport Layer Security(TLS) disallows Man in the Middle, Data tampering attacks. So BSNL scripts cannot be injected without browser identifying and showing error.
Webmaster:
Kindly use Cloudflare's Universal Certificate that is provided free of cost, to protect your users from Greedy ISPs, Hackers & Hacked servers along the network path.
BSNL:
Try to behave professionally, build the confidence & trust with people about your service and you brand name. There should be other legitimate ways to improve revenue but surely not this.
This post was created to make readers to understand or educate them the reason behind the strange redirects on their browsers,. NOT for creating hate against someone or some company.
PS: Still I use BSNL, with the mentioned IPs blocked through the hosts file.
